How to Extract Command Line (CMD process) Data from Malware Documents HD
Most of malware documents (maldocs) uses CMD (cmd.exe) on its VBA macro to launch its next stage, while you can look directly on its VBA macro code, most of the time they are obfuscated and will be needing to spend some time decoding it; also others are password protected VBA Projects which you needed to crack first to be able to read the VBA macro. Hence might cause you a bit of time, depending on knowledge and experience. One quick way to be able to find out what the second stage command/script/file does is by directly examining its CMD process data along with the parameters it uses. Here is a video tutorial on extracting command line data from malware documents. Document samples used are connected to: Trickbot Malware Emotet Malware and IceID Trojan Emotet Malware and Gootkit Trojan Tools used in video: Process Explorer by Microsoft Sysinternal https://docs.microsoft.com/en-us/sysinternals/downloads/process-explorer CMD Watcher by Kahu Security http://www.kahusecurity.com/tools/CMDWatcher_v0.3.7z (password: kahusecurity) Hope this video helped you somehow. Like and subscribe for more video tutorials.
Похожие видео
Показать еще
 HD
HD HD
HD HD
HD HD
HD HD
HD
 HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD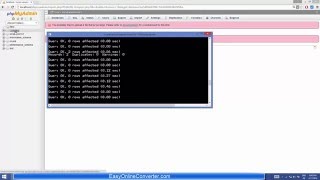 HD
HD
 HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD HD
HD